Advanced Firewall Evasion Techniques with Nmap Scanning
Written on
Chapter 1: Introduction to Network Penetration Testing
In the realm of cybersecurity, organizations frequently conduct penetration tests to evaluate the security of their networks and connected devices. These assessments are vital to ensure that everything complies with established security policies.
Imagine being tasked with a network penetration test, but all you have is a list of IP addresses. Often, companies themselves may not have a complete picture of their internal IP usage. If you lack a pre-defined strategy, your first step will be to scan the provided IP addresses to identify active services. Should this approach fail, you will need to devise your own methodology. Once you have access to the active services, you can begin searching for vulnerabilities to exploit. However, during this process, you may encounter a firewall that blocks the packets generated by Nmap or any other port scanner. What options do you have?
Fortunately, there are various techniques you can employ to bypass firewalls. While not every method will be effective against every firewall configuration, they are worth exploring. In this article, we will discuss two primary evasion techniques and will cover additional strategies in the next installment.
Understanding TCP Stealth, Null, FIN, and Xmas Scans
Method 1: Altering Scan Types
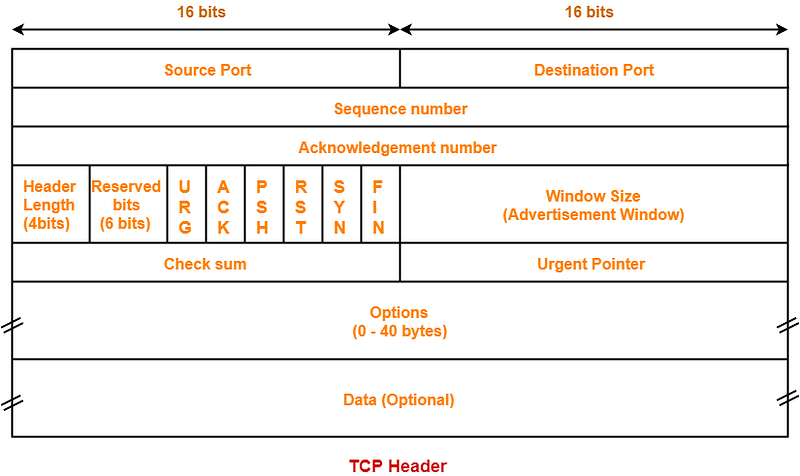
When you initiate communication using the TCP protocol, packets are sent with specific flags set in their headers, such as URG, ACK, PSH, RST, SYN, and FIN. Nmap, by default, employs TCP packets to conduct scans, unless specified otherwise.
TCP Stealth Scan
The TCP Stealth Scan is the default method when running Nmap with administrative privileges. By using the -sS option, this scan type allows for rapid evasion techniques. Unlike standard scans, a TCP Stealth Scan does not complete the TCP handshake; it stops once the server sends a SYN-ACK response, followed by an RST request from the client. This means you can confirm an open port without establishing a full TCP connection.
Syntax: nmap -sS TARGET_ADDRESS
TCP Null Scan
The TCP Null Scan is unique in that all six flags in the packet are set to zero. This results in no response from open ports, while closed ports will respond with a packet that includes the RST flag. Be cautious, as this method can generate false positives.
Syntax: nmap -sN TARGET_ADDRESS
TCP FIN Scan
Similar to the Null Scan, this method sets the FIN flag. An open port will not produce a response, while a closed port will return an RST packet.
Syntax: nmap -sF TARGET_ADDRESS
Custom Scan
Nmap allows for custom scanning techniques using the --scanflag switch, enabling you to set any combination of TCP flags.
Syntax: nmap --scanflag RSTSYNFIN TARGET_ADDRESS
Method 2: Bypassing Firewalls through Source Manipulation
While Nmap may seem like a straightforward scanner, it offers powerful capabilities that can mask your IP address, modify your MAC address, relay scans through proxies, and set specific source ports—all at once.
Using Proxies
Utilizing a proxy or VPN in public networks enhances your anonymity. During a penetration test, routing your TCP/UDP requests through a proxy conceals your real IP address. To use a proxy during a scan, you can employ the following syntax:
Syntax: nmap -sS --proxies 10.10.10.10
Spoofing MAC Address
On certain networks, access is restricted based on MAC addresses. If your MAC address isn’t whitelisted, you can spoof it with Nmap.
Syntax: nmap --spoof-mac 0
Spoofing the IP Address
IP spoofing involves changing the source IP address to one that is part of your network. This technique can help avoid blacklisting.
Syntax: nmap -S 1.1.1.1 TARGET_ADDRESS
Fixing the Source Port Number
If firewalls only accept requests from specific port numbers, you can specify this using the -g or --source-port switch.
Syntax: nmap -g 80 TARGET_ADDRESS
Conclusion
While firewalls can complicate scanning processes, improper configurations may allow for circumvention. In this article, we explored various methods for conducting scans, from TCP SYN scans to IP and MAC address spoofing. Our next post will delve into additional evasion techniques.