Understanding OCSP and Its Integration with F5 Technology
Written on
Chapter 1: The Importance of OCSP
The Online Certificate Status Protocol (OCSP) serves as a vital tool for verifying the validity of digital certificates. Typically, certificates are issued with a specific validity period; however, there are instances when a Certificate Authority (CA) must revoke a certificate. There are three main methods to revoke certificates: CRL (Certificate Revocation List), OCSP, and OCSP Stapling.
This leads us to our first video:
Video Overview: This video discusses the revocation of digital certificates, detailing CRL, OCSP, and OCSP Stapling, providing insight into how these methods function in securing online communications.
Section 1.1: Understanding CRL
In the CRL method, when a client attempts to access a website, the browser queries the CA for the certificate revocation list. If the requested certificate is not listed, the browser accepts it as valid. However, increased traffic to popular sites can overwhelm CA servers. Consequently, if a client fails to retrieve a CRL, the browser may still trust the certificate.
Section 1.2: Advancements with OCSP
OCSP was developed to address the limitations of CRL by utilizing a whitelist rather than a blacklist approach. When a client receives a certificate, the browser queries the CA, which replies with one of three statuses: Good, Revoked, or Unknown. Despite its improvements, this process can still generate significant traffic on CA servers, leading to potential trust issues if the browser does not receive a response.
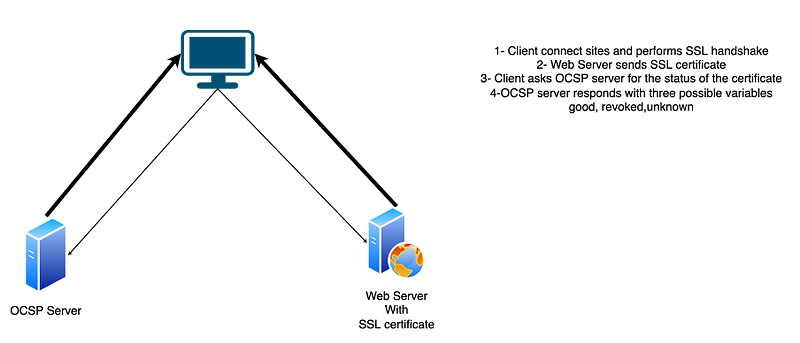
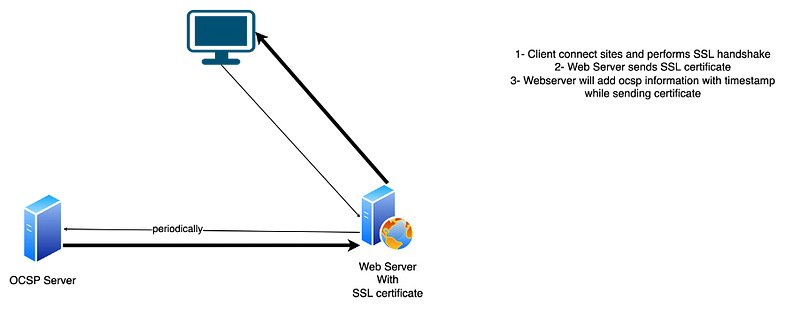
Section 1.3: What is OCSP Stapling?
OCSP Stapling aims to reduce the load on CA servers. In this model, the web server periodically queries the CA for the certificate's status and sends this information during the SSL handshake. This method minimizes the need for repeated queries, enhancing efficiency.
Chapter 2: Configuring OCSP on F5 Systems
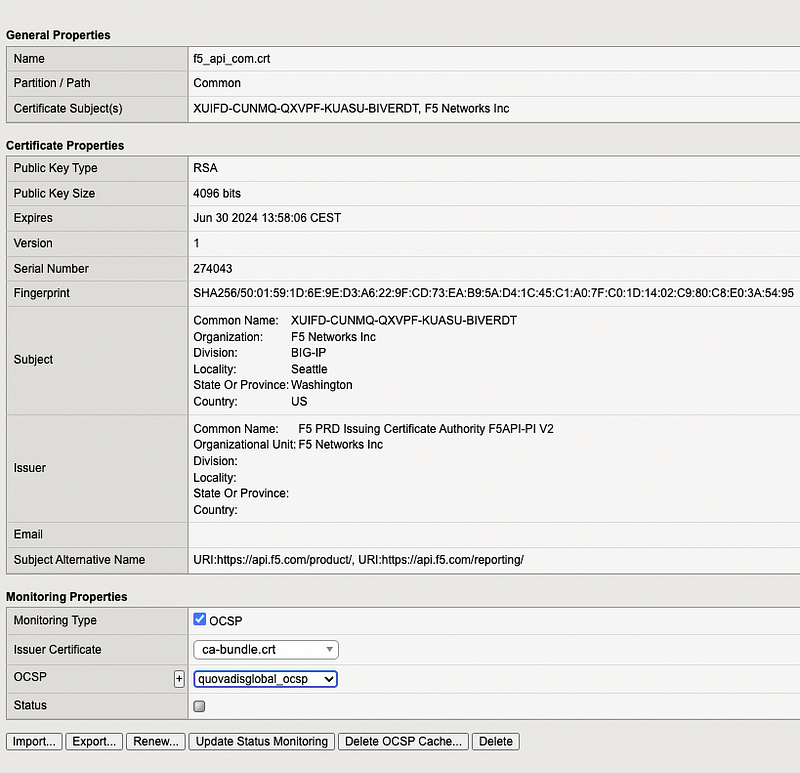
Section 2.1: Creating an OCSP Profile
To create an OCSP profile, navigate to System > Certificate Management > Traffic Certificate Management > OCSP. Here, you can define a new OCSP profile with the following essential parameters:
- Name: Provide a unique identifier for the OCSP profile (mandatory).
- Use Proxy: Check this box if using a server that proxies HTTP requests to an external server; leave unchecked if using a domain name in the OCSP stapling profile’s Responder URL.
- DNS Resolver: Specify the appropriate DNS resolver based on your previous selection or click + to define a new one (mandatory).
- Route Domain: Choose the route domain for fetching OCSP responses using an HTTP forward proxy or click + to define a new route domain.
- Concurrent Connection Limit: Set the maximum number of connections per second allowed for OCSP certificate validation, defaulting to 50.
Section 2.2: Adding Monitor to SSL Certificate
To ensure the OCSP profile functions correctly, associate it with the SSL certificate used in the Client SSL profile. Navigate to System > Certificate Management > Traffic Certificate Management > SSL Certificate List, and select the Monitoring Type checkbox to monitor the SSL certificate's revocation status.
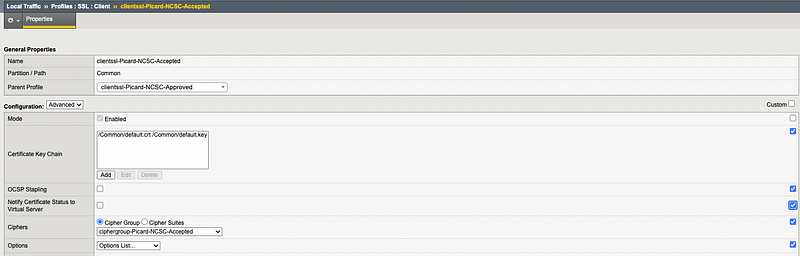
Section 2.3: Enabling OCSP on Client SSL Profile
Go to Local Traffic > Profiles > SSL > Client. Enable OCSP stapling and associate the CA certificate used to sign the OCSP responder certificate with the Client SSL profile. Enable the Notify Certificate Status to Virtual Server option to communicate the SSL certificate revocation status.
To further enhance your understanding, here’s another relevant video:
Video Overview: This video explores the implementation of SSL Everywhere, providing insights into the significance of secure connections in today's digital landscape.
Join FAUN: Website ?|Podcast ??|Twitter ?|Facebook ?|Instagram ?|Facebook Group ??|Linkedin Group ?| Slack ?|Cloud Native News ?|More.
If you found this article helpful, consider clicking the clap ? button below to show appreciation for the author ?.